Grow faster, together.
Discover a new path to business growth, powered by effortless collaboration and communication with your partners, distributors, and resellers.

Grow faster,
together.
Discover a new path to business growth, powered by effortless collaboration and communication with your partners, distributors, and resellers.

Making things as seamless as possible.
It’s more about the journey...
Give your partners the best experience possible with the suite of products offered by Impartner.
Recruit
Drive traffic of potential new partners to the partner registration process via email campaigns and public-facing web pages. Leverage the configuration abilities of Impartner to create messaging to entice the right type of partners to apply for access.
Enroll
Easy application process for potential partners that leads to a sophisticated approval workflow system so that you can carefully select who gets to pass through the velvet rope and be welcomed into your exclusive content and toolset provided to your authorized partners.
Onboard
Getting your partners onboarded and provided with portal credentials is only the beginning. You need to truly guide each partner through their journey that will drive them to their first dollar of revenue generated for you. Doing so in an automated, scalable fashion will provide a consistent and repeatable experience.
Train & Enable
Curate and present professional training material to the right partners at the right time that facilitates testing to confirm competency. The better trained a partner is on your products, the better they can sell and support those products, and the happier your customers will be.
Manage Pipeline
Make it easy for your partners to register deals and have the data sync in real-time to your CRM to resolve channel conflict. Also, have a well-defined delivery process of pre-qualified leads to your high performing partners to carry until close.
Sell
Provide all the sales and marketing materials within Asset Library that are needed to assist partners to be successful, including enabling co-branding or white labeling of any documents of your choosing. It’s important to make these materials easy to find with in-document search and simple to preview, download, or share with one-click options.
Generate Demand
Amplify your marketing messages by extending lead generation campaigns to your partners’ networks with our low-touch methodology, which maximizes your reach by simplifying and automating adoption. No matter the source, you will have full lead attribution for a complete ROI picture and reliable delivery methods to get hot leads into partners’ hands immediately.
Through Channel Marketing Automation (TCMA)
Market Development Funds (MDF)
Impartner Marketplace
Engage & Communicate
Successful channels know the importance of remaining in regular communication with your partners. The best channels provide 100% personalized and targeted content in a highly scalable and cost-effective manner to deliver far better audience engagement. When executed properly, you up-level your partners to be experts of your brand.
Motivate & Reward
Partners are mostly coin-operated, so it’s imperative that you provide a clear and simple picture of the rewards they stand to gain for being successful with you. The levels of access, benefits and progress of rewards need to be spelled out plainly to your partners to keep them motivated.
Plan & Optimize
It’s said that without goals, and plans to reach them, you are like a ship that has set sail with no destination. This is especially true for your partners. Create business plans where partners and their channel managers can both track progress toward stated goals in real time and avoid an unpleasant QBR surprise.
Measure
Analyze what’s working and what’s not across every aspect of your indirect sales with the same insight you have into direct sales. All key aspects of your Impartner platform are collected into pre-packaged reports – sales pipeline, asset engagement, journey or training progress – or create your own personalized reports and dashboards to get the exact data that you need to identify successful partners or areas for possible improvement.
Recruit
Drive traffic of potential new partners to the partner registration process via email campaigns and public-facing web pages. Leverage the configuration abilities of Impartner to create messaging to entice the right type of partners to apply for access.
Enroll
Easy application process for potential partners that leads to a sophisticated approval workflow system so that you can carefully select who gets to pass through the velvet rope and be welcomed into your exclusive content and toolset provided to your authorized partners.
Onboard
Getting your partners onboarded and provided with portal credentials is only the beginning. You need to truly guide each partner through their journey that will drive them to their first dollar of revenue generated for you. Doing so in an automated, scalable fashion will provide a consistent and repeatable experience.
Train & Enable
Curate and present professional training material to the right partners at the right time that facilitates testing to confirm competency. The better trained a partner is on your products, the better they can sell and support those products, and the happier your customers will be.
Pipeline
Manage Pipeline
Make it easy for your partners to register deals and have the data sync in real-time to your CRM to resolve channel conflict. Also, have a well-defined delivery process of pre-qualified leads to your high performing partners to carry until close.
Sell
Provide all the sales and marketing materials within Asset Library that are needed to assist partners to be successful, including enabling co-branding or white labeling of any documents of your choosing. It’s important to make these materials easy to find with in-document search and simple to preview, download, or share with one-click options.
Demand
Generate Demand
Amplify your marketing messages by extending lead generation campaigns to your partners’ networks with our low-touch methodology, which maximizes your reach by simplifying and automating adoption. No matter the source, you will have full lead attribution for a complete ROI picture and reliable delivery methods to get hot leads into partners’ hands immediately.
Through Channel Marketing Automation (TCMA)
Market Development Funds (MDF)
Impartner Marketplace
Communicate
Engage & Communicate
Successful channels know the importance of remaining in regular communication with your partners. The best channels provide 100% personalized and targeted content in a highly scalable and cost-effective manner to deliver far better audience engagement. When executed properly, you up-level your partners to be experts of your brand.
Reward
Motivate & Reward
Partners are mostly coin-operated, so it’s imperative that you provide a clear and simple picture of the rewards they stand to gain for being successful with you. The levels of access, benefits and progress of rewards need to be spelled out plainly to your partners to keep them motivated.
Plan & Optimize
It’s said that without goals, and plans to reach them, you are like a ship that has set sail with no destination. This is especially true for your partners. Create business plans where partners and their channel managers can both track progress toward stated goals in real time and avoid an unpleasant QBR surprise.
Measure
Analyze what’s working and what’s not across every aspect of your indirect sales with the same insight you have into direct sales. All key aspects of your Impartner platform are collected into pre-packaged reports – sales pipeline, asset engagement, journey or training progress – or create your own personalized reports and dashboards to get the exact data that you need to identify successful partners or areas for possible improvement.
Optimize
Power your channel
with our partner relationship management tools.
Amplify
Deliver on the promise of
partner demand generation with powerful marketing automation.
Communicate
Personalize partner
communication via email
and social media.
Unlock significant growth with Impartner
A commissioned study conducted by Forrester Consulting found that a composite organization based on Impartner customers achieved the following:
296%
return on investment over 3 years
Up to 50%
increase in partner-sourced deals
$2.4M
net value over 3 years

Impartner is rated #1 by customers on G2
We’re rated #1 overall on G2 for enterprise partner relationship management, over Salesforce, Zift, PartnerStack, Mindmatrix, Allbound, and more.
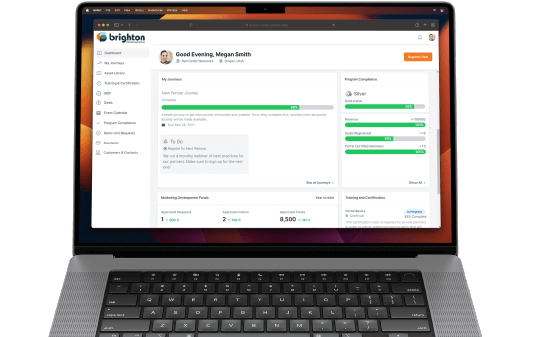
We give you the big picture
with no blind spots
We give you the big picture
with no blind spots
Consolidate a full range of powerful tools into a single view so you can track every detail and drive partnership growth.

It’s like we were destined
to be together.
Seamless integration with the world’s leading CRM platforms takes business-as-usual to a whole new level.
It’s like we were
destined to be
together.
Seamless integration with the world’s leading CRM platforms takes business-as-usual to a whole new level.
We can’t stop making headlines.
There’s always something new at Impartner. Keep up with the latest!

Watch Multiply: ImpartnerCon '24 Sessions

Ryan Knapp Named CRN Channel Chief
Named Leader in Forrester Wave
Mike Kirby on Partner Data
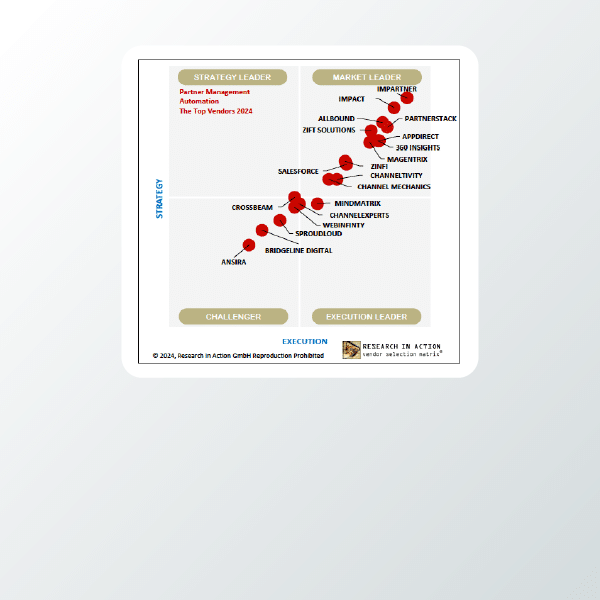
Named #1 Partner Management Automation Vendor
#1 Overall PRM on G2
2023 Visionary Spotlight Award Winner

Gary Sabin on Customer Experience

Impartner® Gold Stevie Award
*Results from a commissioned Total Economic Impact™ analysis conducted by Forrester Consulting.
It’s time to grow faster, together.
At Impartner, we make powerful partner networks unstoppable, with organizations achieving 296% ROI and 50% more partner-sourced deals. Ready to see how it works?
Fill out the form to pick a date and time for your demo.
All fields are required.
Thank you for getting in touch!
More partner revenue, and less work? We love that for you. We can’t wait to help you grow your ecosystem. One of our partner experts will be reaching out shortly.
Have a great day!